10 Essential Steps to Protect Your Website from Hackers
Every website needs security because businesses rely more on digital platforms. Cybercriminals are always watching for weak spots; a single weak spot in security lets thieves steal information. Also, this can disrupt services and bring years of harm to a reputation. This article tells you about the top 10 steps you can take to prevent your website from getting hacked. It will also enable you to boost website performance with some shared tips that enhance security with speed.
These practical steps apply to every kind of online platform. You can use them for personal blogs to enterprise-level ecommerce development projects. Whether you are venturing into website development for the first time or working with the best website development companies, these applicable tools will work for everyone.
Strengthening Website Development with 10 Must-Follow Security Steps
- Implementation of HTTPS and Acquisition of an SSL Certificate

The primary point between the web and a secure platform is HTTPS. All data travelling between your visitors and your website is encrypted by HTTPS. This includes everything from logins and payments to personal information. Besides, you can get an SSL certificate for free from companies like Let's Encrypt. You can also purchase an advanced one, like EV or Wildcard SSL, for enterprise-grade protection. HTTPS and SSL make your website secure. It helps create better trust and, in turn, faster web development.
Example: Therefore, SSL and HTTPS can prevent a small e-commerce site from leaking credit card data to attackers by blocking man-in-the-middle attacks
- Set up a Robust Web Application Firewall (WAF)

The prime objective of this WAF is to filter malicious traffic directed towards your web. Additionally, securing your website firewall security services is always a good choice. With a reliable Web Application Firewall service in place, you can easily provide much-needed security. Even if an attacker tries to carry out SQL injection, DDoS, XSS and various other attacks, a WAF can analyse. It can also filter the HTTP traffic of such related attacks.
Example: If a hacker tries to inject a script into a form field, the WAF will detect it and neutralise it before it gets anywhere near harming the system. Also, on the competitive side, services such as Cloudflare and Sucuri provide built-in performance-improving features.
- Setting up a Content Security Policy (CSP)
CSPs specify where resources on your website can be loaded from, such as scripts, stylesheets, or fonts. Also, implementing CSP for secure website development in India ensures no attackers can inject harmful code, say via cross-site scripting.
Example: Your CSP can configure an allowance for JavaScript from only your domain and trusted CDNs to block suspicious third-party scripts that want to hijack user sessions or scrape data
- Regularly Update Your Website Platforms, Plugins, and Scripts
Software providers always offer patches for vulnerabilities. Ignoring such updates opens one to exploitation. Regular Refreshing is important for safe and optimised Website Development.
Example: An outdated WordPress plugin can be compromised by a known vulnerability. Regular updates–automated wherever possible–can stop easy breaches.
- Strengthen Your Admin and User Passwords
Weak passwords are a hacker's simplest entry point. Use a long, complex password enforced by rules such as changing it after certain intervals. Improving password practices for secure e-commerce development is a potent tool.
Example: Instead of "admin123," try using something like "!Adm1n#2025Secure$." Password managers like 1Password help you generate and save these strong credentials safely.
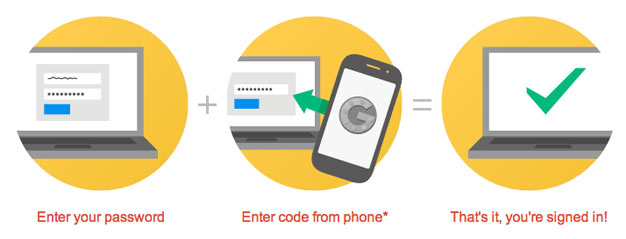
- Enabling Two-Factor Authentication - 2FA
2FA adds a secondary verification step beyond the normal password input, in most cases requiring the user to enter a temporary code sent to their phone or generated by an application. This is done to block attackers from using stolen login credentials. Use two-factor authentication to boost website performance and security.
Example: Even though they may have somehow acquired your administrator password, the chances of getting in without having access to your 2FA device or code are less, and as such, it dramatically enhances security.
- Performing Regular Malware/Vulnerability Scans
Use scanning tools like Wordfence (for WordPress), Sucuri SiteCheck, or Qualys SSL Labs. These tools check your site for malware, old components, and suspicious activity. Use tools that scan for malware for secure Magento website protection to achieve a highly secure website.
Example: A malware scanner can tell you if a file on your server has been altered to redirect traffic to a phishing site, allowing you to intervene before this becomes a problem for your visitors.
- Regular Backup of Your Site

The backups serve to save from falling danger net. Thus, the backup is automated daily and stored off-site or on some dependable cloud platforms. Have a plan in place to restore it once your site crashes. In terms of data, backup is the only protection available, and page speed improvements are always the best prevention option.
Example: If hackers lock your server for ransom, a fresh backup lets you wipe the system clean and restore everything—without paying any money.
- Speed Optimised Site Structure with Security

Speed always improves the user's experience and also lowers the risk. Blend website speed optimisation with intelligent site architecture. A website that loads fast has fewer points for interception, thus more difficult for harmful scripts to find weaknesses.
Example: By combining 'minifying' JavaScript and CSS and conditioning impact images, you not only decrease your attack surface but also receive a better ranking from the search engines.
- Work with Trusted Web Development Experts
A proficient website developer would successfully implement ways to incorporate security into every layer of your site, whether it is the back-end database or front-end assets. Make sure to partner with the website designing company India for Security
Example: A trusted development team would ensure secure login on the site, plus server-side validation against unsafe data imports to create a solid foundation.
Why User Education Is a Critical Element of Secure Website Development
Technical defences are important to have, human failures continue to be one of the most common occurrences of website breaches. Team training on secure website development India practices can become a game changer for the security of your platform and the overall website security strategy.
Training and Management of the Staff Access

Train the team in identifying emails allegedly sent phishing, using secure passwords, and recognising suspicious activities. The education is integrated into your web design services, so employees will be aware of the risks and know how to respond to them.
Limit admin privileges for confidential files, and assign access based on roles; the ‘least privilege’ principle is vital for maintaining the website firewall security services, to ensure that an attack involves only one account at most.
- Security Culture Creation
A proactive mindset about security can prevent a lot of avoidable incidents. Regularly changing password policies, multi-factor authentication across all admin logins, and setting up open lines of communication for reporting are key ingredients.
Make cybersecurity training part of the onboarding and continuing education of your employees; therefore, they form a team for website speed optimization and defence of your website.
- Education for Users
For security purposes, if your platform collects data from users or processes transactions like an e-commerce development site–give clear prompts to your users on safe practices.
Add a meter signup and warning when sensitive information enters on unsecured pages. It reminds users not to reuse passwords across sites and helps to instil user trust and strengthen usability, they would also serve to boost website performance.
- Regular Security Audits and Simulations
Regularly conduct security audits and simulated attacks to test both your systems and your team. Some of the basic tools in ensuring core web vitals optimization and the early identification of vulnerabilities include periodic phishing attack simulations, user behavior analysis, and access log audits.
This regular assessment—preferably done by some of the elite website development companies ensures your defence mechanisms keep evolving with the responsibilities of the newly generated threats.
Adding user education into the mix provides yet another layer of protection that can't be provided purely by software. A security-conscious team, combined with professional web design services, provides a robust foundation for a secure and performant site.
Bonus Tips: Performance + Security Go Hand-in-Hand
Remember to always take notice of both aspects: security and performance. Here are ways to align the two objectives -
- Improve website loading speed India by image compression and smart caching techniques.
- Reduce website load time with lazy loading and code minification.
- All metrics in core web vitals optimization have to be addressed to keep consumers happy and against performance-related attacks.
The more optimized the website, the less exposure to compromise. It's a win-win situation for your visitors and your security team.
Conclusion

Cyber threats are increasing every minute, so the security around your website must be upgraded every minute. These 10 steps provide the measures to secure your online domain, always keeping in mind security and performance.
Switching to HTTPS, configuring Content Security Policy, and using website firewall security services are options that can provide extra layers of security to your enterprises. These steps go beyond just eCommerce development or managing high-traffic Magento sites—they help you stay one step ahead of hackers.
Do you need help in implementing the above-mentioned steps? A top-rated website design company India will be the one for you because your digital assets deserve nothing less.






Comments
Be The First To Comment
Post a comment